In my previous post https://www.leogether.com/2022/01/create-azure-ad-app-registration-using.html, I wrote about creating app registration programmatically. In this post, I will aim at creating multiple app roles via PowerShell script that uses Azure AD PowerShell commands that in turn uses MS Graph behind. App roles are usually defined on application registration representing a service, app or API.
This article assumes you have knowledge of App registration, just giving a brief overview about app roles to start with.
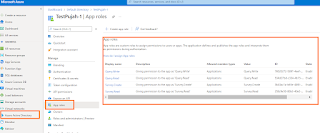
When a user signs in to the application, Azure AD emits a roles claim for each role that the user or service principal has been granted individually to the user and from their group membership. This can be used to implement claim-based authorization. App roles can be assigned to a user or a group of users. App roles can also be assigned to the service principal for another application, or to the service principal for a managed identity.
Once you've added app roles in your application, you can assign users and groups to the roles. When the users assigned to the various app roles sign in to the application, their tokens will have their assigned roles in the roles claim.
Similarly, you can assign an app role to a client app. When you assign app roles to an application, you create application permissions. Application permissions are typically used by daemon apps or back-end services that need to authenticate and make authorized API calls as themselves, without the interaction of a user.
For programmatically creating app roles, I have created a script in my GitHub repository — CreateAppRoles.ps1
My GitHub repository link is:
https://github.com/Pujago/ApplicationRegistrationUsingMSGraphAPIs-Public
How the script works?
- CreateAppRoles.ps1 will first authenticate to Azure AD (using script ConnectToAzureAD.ps1)
- Once authenticated, it will create the app roles.
Note: CreateAppRoles.ps1 requires ConnectToAzureAD.ps1 to be in the same folder.
Before using script:
If you have not read my previous post, please click here https://www.leogether.com/2022/01/create-azure-ad-app-registration-using.html to follow the sections for:
- Pre-requisites
- Create master App Registration
If you have already done that, you do not need to repeat the above steps.
How to run the script?
Please follow the steps below to use the repository:
- Go to the link: https://github.com/Pujago/ApplicationRegistrationUsingMSGraphAPIs-Public
- Clone the repository.
- Open the powershell terminal, go to the repository location, go to scripts folder.
Connect to Azure account:
$ServicePrincipalPW="<Master app registration client secret>"
$passwd = ConvertTo-SecureString $ServicePrincipalPW -AsPlainText -Force
Run the script:
In my next post, I will be writing about how to create scopes to expose web API registration programmatically. Till then, happy reading.




Play Real Money Slots Online - JamBase
ReplyDeleteFree Slots No Download needed 시흥 출장샵 & 전라남도 출장안마 250000 화성 출장샵 Free Coins Welcome Bonus to JamBase! Play 제천 출장샵 Online Slots 서산 출장안마 & Games with Free Signup or Download.